Managing Login Failure Daemon (LFD) from DirectAdmin
Login Failure Daemon popularly known as LFD comes with the ConfigServer Security & Firewall. At KnownHost all the managed services are being deployed with ConfigServer Security & Firewall as software based firewall and basic monitoring system to avoid unwanted attacks and the notification of certain events. LFD perticularly track and log the activities which are happening on the server to the CSF (ConfigServer Security & Firewall). The list of activities LFD handels is as below,
- Processes running longer than X seconds
- Processes utilizing too much memory
- Processes from specific user higher than X allowed
- Invalid login attempts against SSH, FTP, IMAP, SMTP, and more
- Various other blocking configurations from integrations such as mod_security.
Accessing the LFD Plugin
First, to login into the DirectAdmin control panel as Admin User,
https://your-domain.com:2222 or https://IP-address:2222 or https://server-hostname:2222.

Navigate to Extra Features → ConfigServer Security & Firewall.
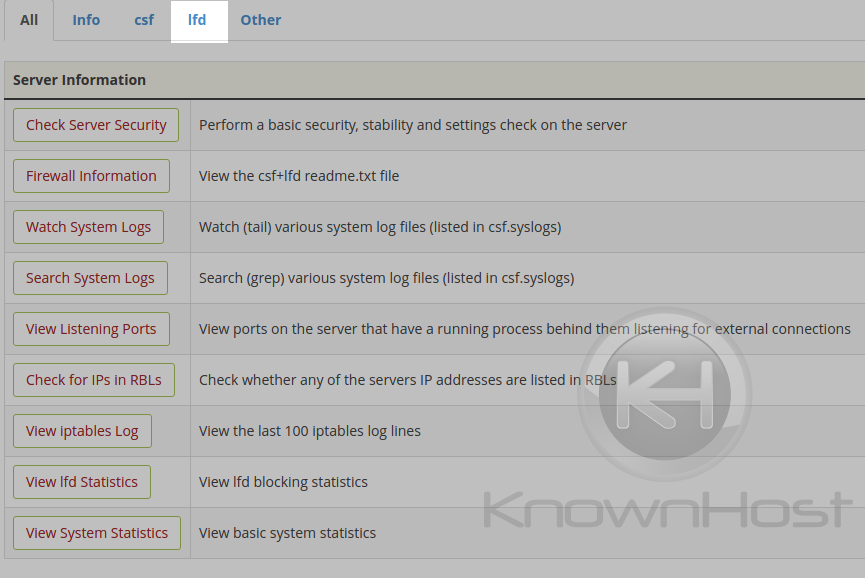
Within this section, you can click the ‘lfd’ tab at the top which will show you only options and configurations related to the Login Failure Daemon.
- lfd Status
- lfd Restart
- lfd Ignore file
- lfd Directory File Watching
- lfd Dynamic DNS
- lfd Alert templates
- lfd Log Scanner Files
- lfd Blocklists
- lfd Syslog Users
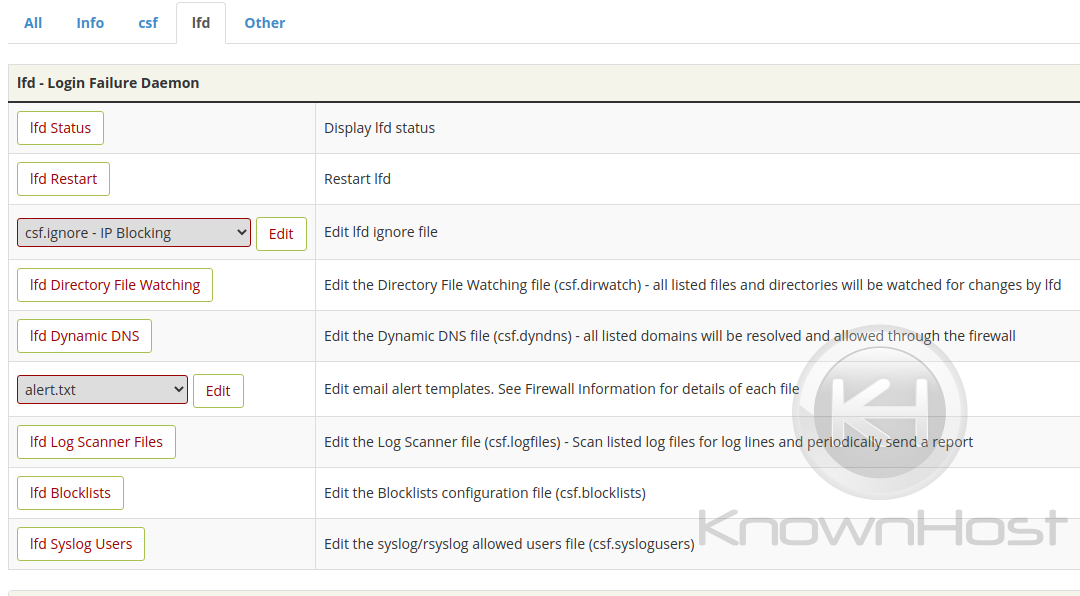
lfd Status
The ‘lfd Status’ provides the systemd details of the ‘lfd.service’ running on your server. You’ll see whether or not it’s actively running, recent log entries regarding it and whether or not the service is experiencing issues. i.e; not starting
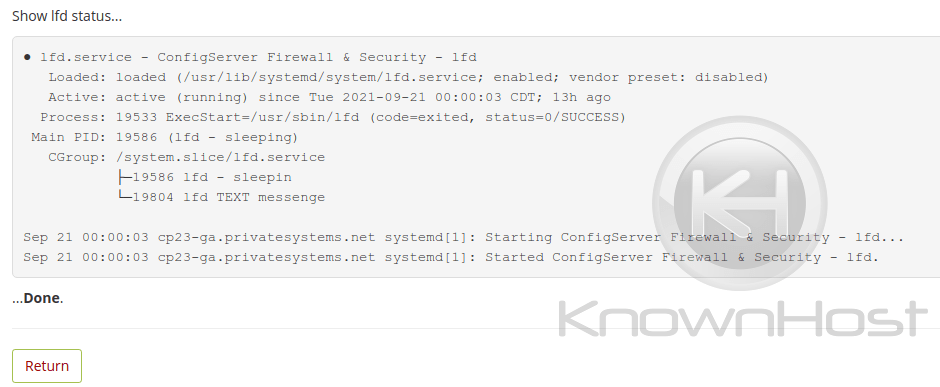
lfd Restart
The ‘lfd Restart’ issues a reboot to the ‘lfd.service’ running on your server. This is recommended after any sort of adjustment to the lfd configuration to ensure that the service has updated with the new config parameters.
lfd Ignore File
The ignore section of the Login Failure Daemon allows you to whitelist things such as IP Addresses, processes, directories, scripts and more. It allows detailed control over what shouldn’t be of concern.
- csf.ignore — Allows the ignoring of IP Addresses that experience incidents such as password failures.
- csf.pignore — Allows the ignoring of processes that shouldn’t be tracked (such as long-running processes, i.e mongod)
- Example path such as ‘exe:/usr/local/bin/mongod’
- Example user such as ‘user:nobody‘ which would then ignore all processes by the nobody user.
- csf.fignore — Allows the ignoring of directories should Directory Watching be configured for a specific file path
- Requires full path or perl regular expression pattern matching.
- csf.signore — Allows the ignoring of specific scripts that are going to be knowingly ran (i.e smtp mail scripts)
- csf.rignore — Allows the ignoring of Reverse DNS Lookups if CSF is blocking crawlers (such as googlebot, bing, etc)
- csf.suignore — Allows the ignoring of superusers against the LF_EXPLOIT SUPERUSER check.
- csf.migore — Allows list of users and local IPs to be ignored by the RT_LOCALRELAY_ALERT check.
- csf.logignore — Allows usage of regex to match logs to be ignored by LOGSCANNER
- csf.uidignore — Allows list of User ID’s(UID) to be ignored by the User Tracking Function.
Should any of the above ignore lists be modified, you’ll need to restart the LFD & CSF Service for the changes to apply.
lfd Directory File Watching
Modifying this file (csf.dirwatch) allows for you to set a list of files and/or directories that you want to watch for changes. Any modifications made to the files listed will send an alert to the notification contact on the server (usually root contact).
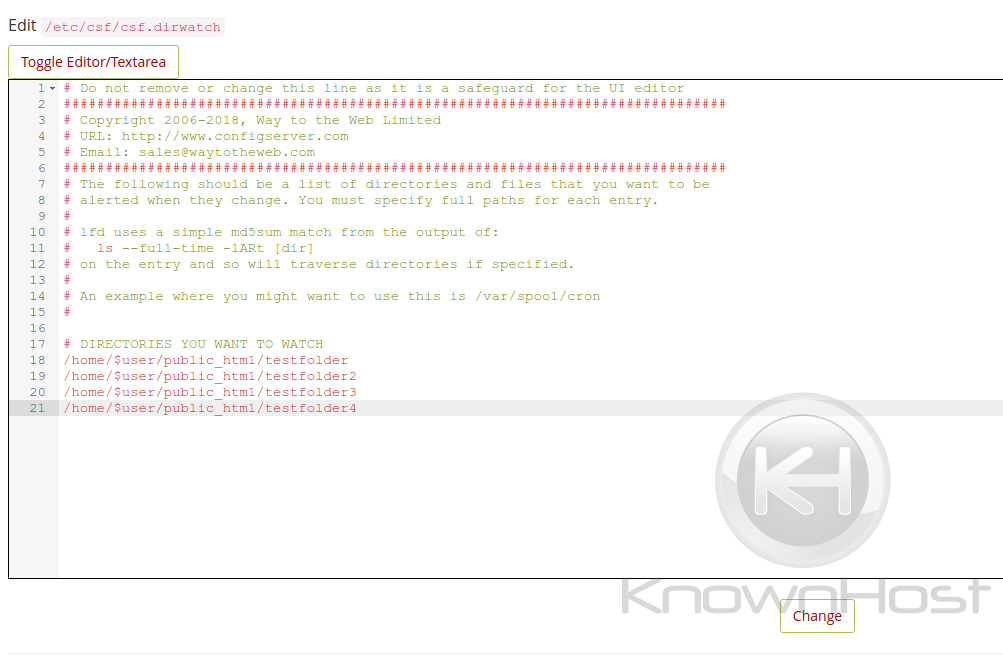
Full paths must be specified in as outlined in the above image.
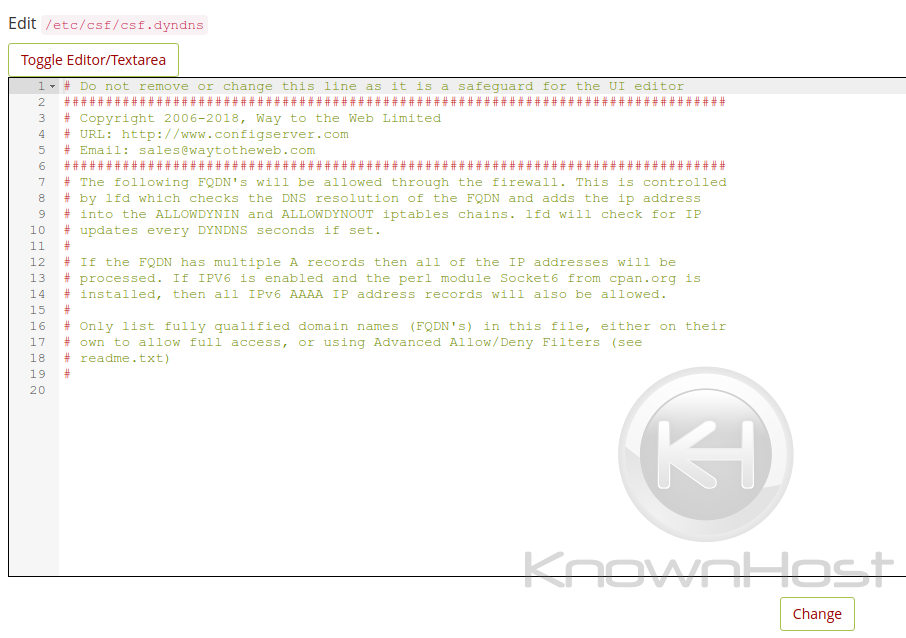
lfd Dynamic DNS
Any listed domains within this file (csf.dyndns) will be resolved and allowed through the firewall. This is useful for those situations where you are using a dyndns service such as no-ip.com and don’t want to constantly whitelist your IP Address.
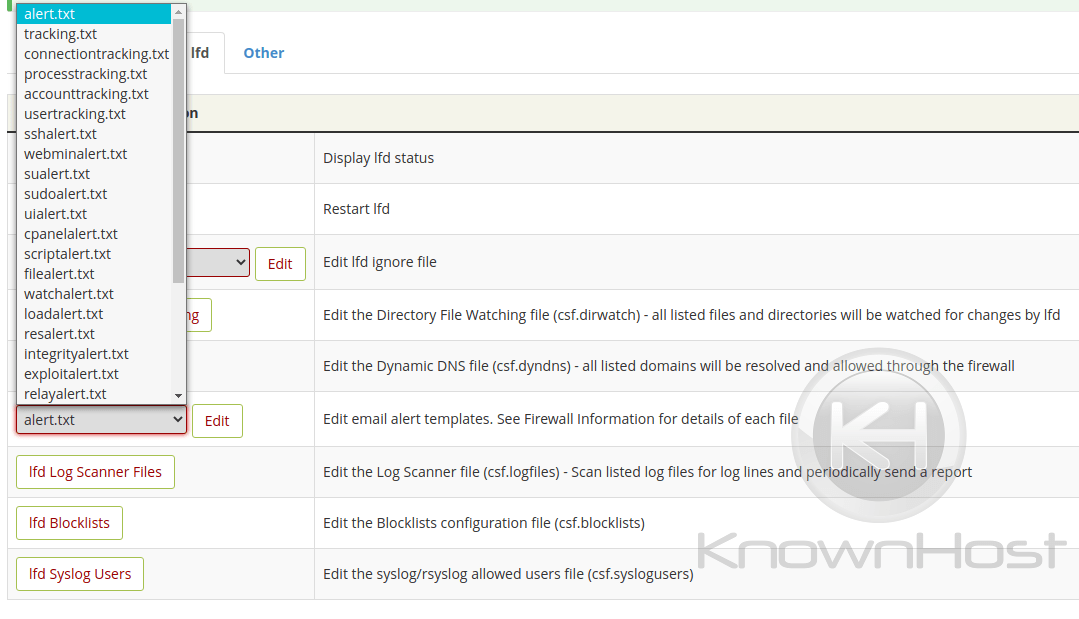
lfd Alert Templates
The Login Failure Daemon provides templates for each alerts and tracking notifications that it sends in regards to login attempts and failures. You can edit these templates to remove or include information that you may or may not find necessary. Clicking the drop down will provide a list of the template files.
lfd Log Scanner Files
This file (csf.logfiles) lists the log files that you wish to have scanned by LOGSCANNER. If enabled, the lfd service would then send a periodic report based on what was scanned.
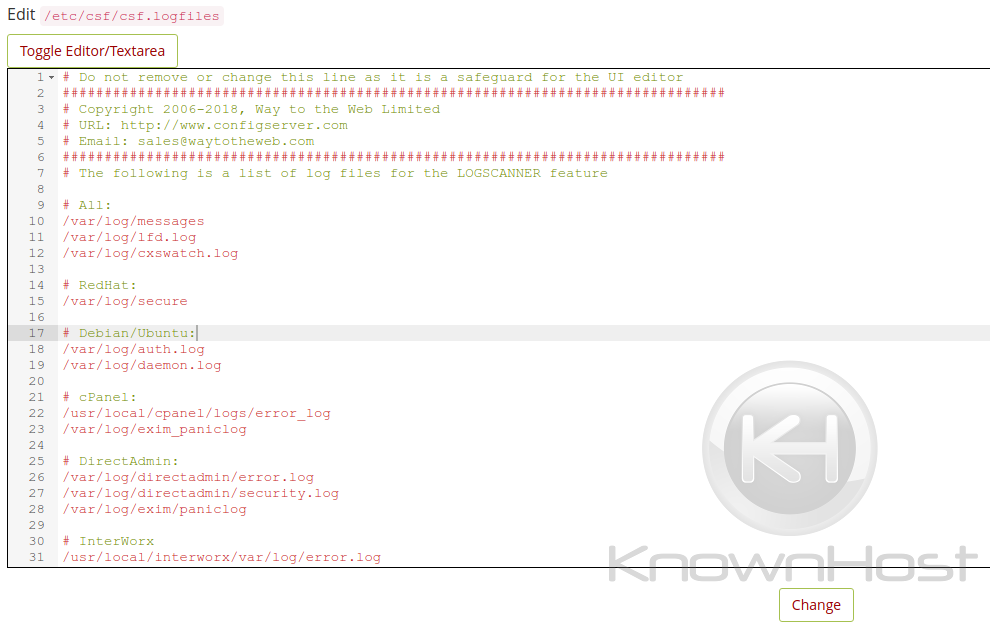
Should the above logscanner file be modified, you’ll need to restart the LFD & CSF Service for the changes to apply.
lfd Blocklists
This file (csf.blocklists) allows the modifying of specified blocklists within lfd/csf. Allowing for the automatic blocking of IP’s within those blocklists. i.e; spamhaus, tor clients, maxmind, etc
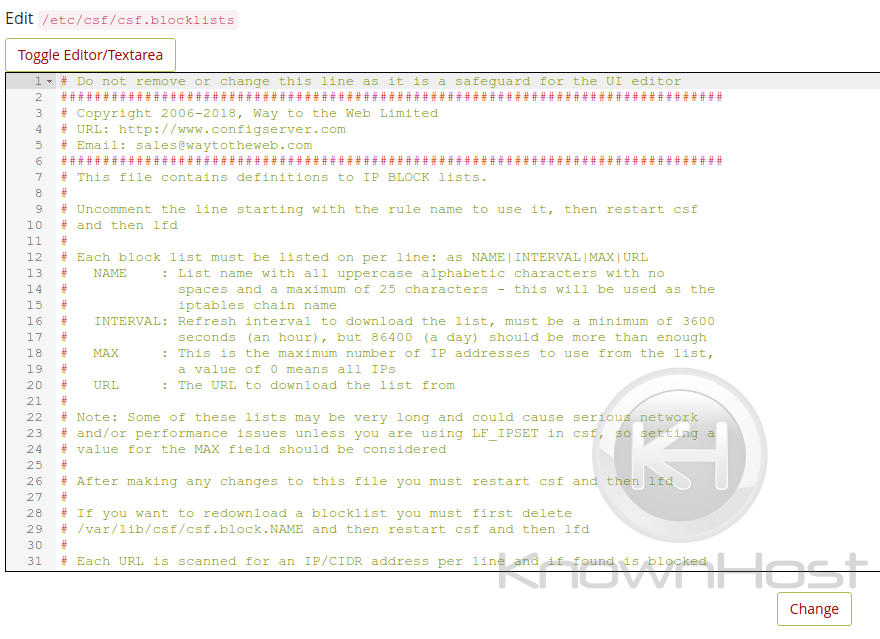
Should the above blocklists be modified, you’ll need to restart the LFD & CSF Service for the changes to apply.
lfd Syslog Users
This file (csf.syslogusers) allows the modification which users are allowed to login to syslog/rsyslog. Users added here get added to the system group. This file doesn’t generally need to be touched.
Conclusion
Managing the Login Failure Daemon section from within DirectAdmin isn’t that hard thanks to the UI provided by the plugin developer. Given what we’ve gone over, you should have a general idea of what everything is and what each feature does. We hope that this was helpful in
KnownHost offers 365 days a year, 24 hours a day, all 7 days of the week best in class technical support. A dedicated team ready to help you with requests should you need our assistance. You’re not using KnownHost for the best webhosting experience? Well, why not? Check with our Sales team to see what can KnownHost do for you in improving your webhosting experience.