How to use Dynamic DNS to automatically whitelist your IP?
Dynamic DNS offers a resolution to a common problem that many users have. ISP’s constantly change their IP, and for one reason or another, they get blocked by their server’s firewall. Often, it’s not the user’s fault. Its not that they are logging in 40 times with the wrong password, but rather they’ve simply exceeded the firewall’s max_connections while developing their sites, or they’ve updated their email account’s password as they should often do, and forgotten to update it also in their mail client, which is repeatedly attempting to access that account on the server using the old credentials. These situations can happen to any of us and result in a firewall block. Thus, many opt to whitelist their IP in the firewall. But, without a static IP, this option isn’t exactly wise. We don’t want to end up with a large number of IPs whitelisted … IPs that the ISP has since assigned to someone else (someone that could potentially have unlimited access to our server). We would have to temporarily whitelist the current IP assigned to us each time it changes and knowing each time it changes is unlikely. Luckily, there is software that can help.
Dynamic DNS is a software that integrates nicely with CSF/LFD firewall that effectively whitelists dynamic IPs. via a hostname you choose. A quick overview of the steps is below. Underneath the quick overview, we will discuss each of the steps in detail.
- Register at np-ip for free dynamic DNS
- Setup a hostname.
- Install the Dynamic Update Client from No-IP on your computer and connect it to the account you just created.
- Open “csf.dyndns” and add the hostname of your no-ip account.
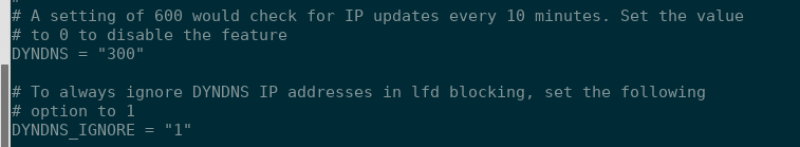
- Open “csf.conf” and set DYNDNS to whatever interval you’d like the check for a new IP to run ( e.g. DYNDNS = “300” would check for IP updates every 5 minutes) and set DYNDNS_IGNORE = “1” to always ignore DYNDNS IP addresses in lfd blocking
- Restart the firewall
Register with NO-IP for free dynamic DNS (Steps 1 and 2)
When you first visit www.no-ip.com, you will see a prompt to enter your desired hostname at the bottom of the page:
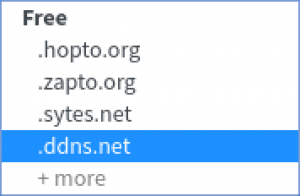
There is a drop-down window so that you can select what TLD you want:
Enter your desired hostname and then click “Sign Up”. You will then need to complete the sign-up process by entering an email account, a password, and confirming the hostname you’d like to use:
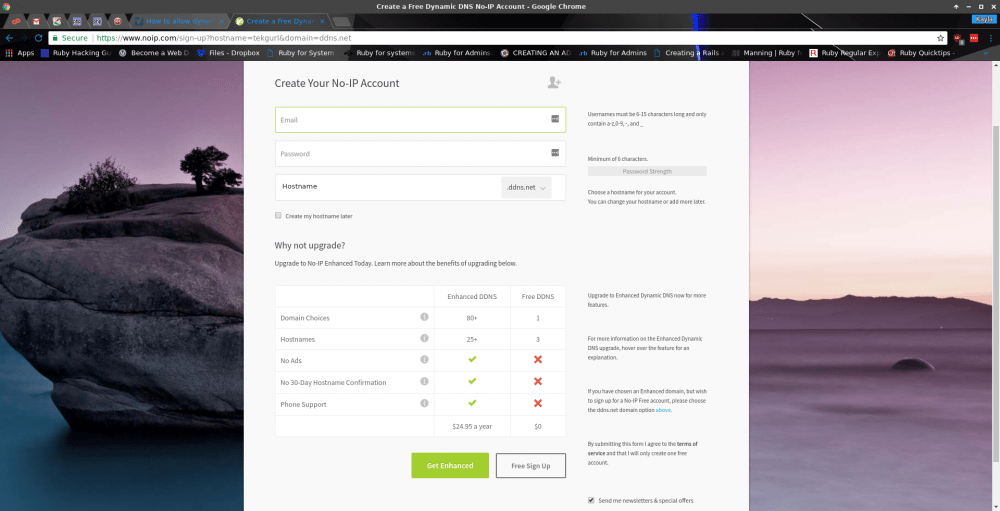
Free Dynamic DNS hostnames must be confirmed every 30 days or they will be deleted.
Create the account, and then you will be sent an account confirmation email:
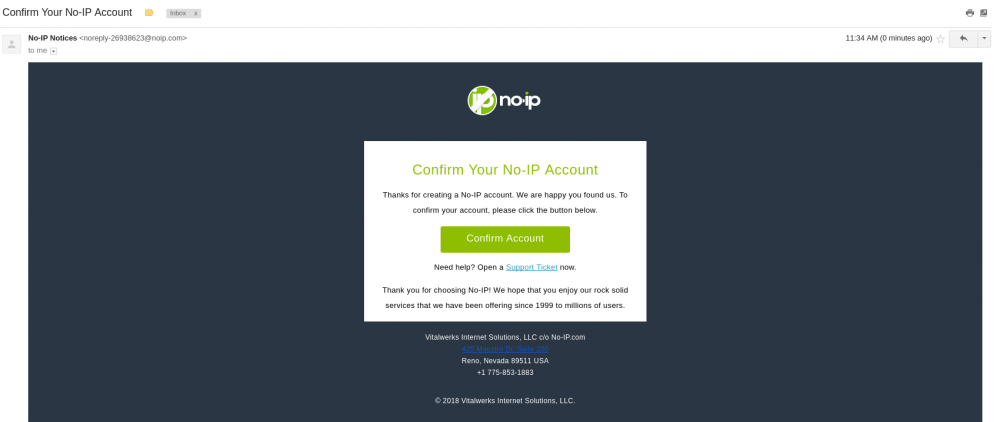
Click to confirm the account. You will be redirected to a new window displaying the message “Your account is now active!” and the following:
Since you are not self-hosting services from your computer, you should not need to set up any port forwarding via your router. You will need to download the Dynamic Update Client and then configure CSF/LFD firewall on your server, though. Let’s move on.
Install Dynamic Update Client (Step 3)
You can download the software via the following link:
Download Dynamic Update Client
If you are using Linux on your computer, you can use the following commands via terminal to install this:
cd /usr/local/src/
wget http://www.no-ip.com/client/linux/noip-duc-linux.tar.gz
tar xf noip-duc-linux.tar.gz
cd noip-2.1.9-1/
make installHere is the what this installation looks like on mine:
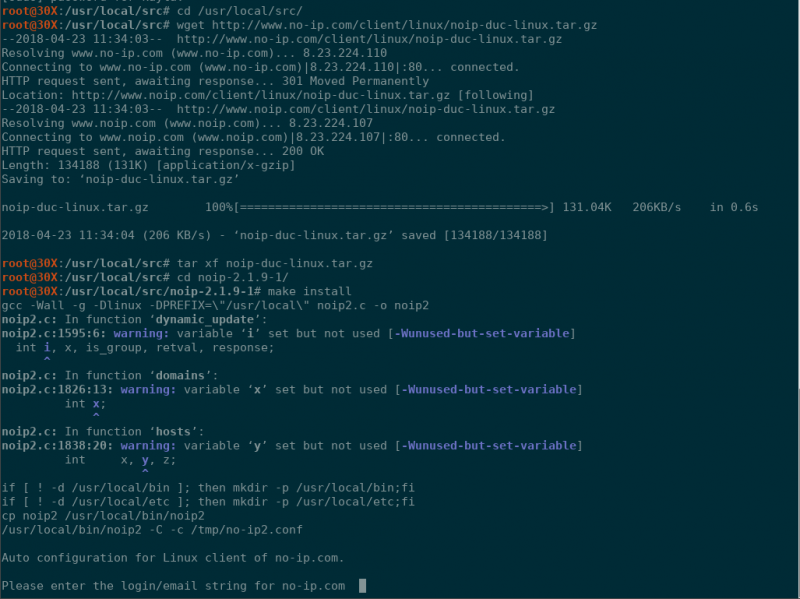
Notice that this installation is not yet complete, though. The last line is a prompt for your account information. You will enter your email, your password, and your hostname as prompted to complete the installation.
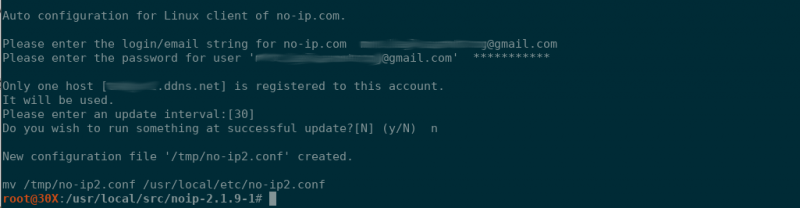
The installation of the Dynamic Update Client should now be complete. At this point, you should be able to dig the hostname you created and see an A record for it like so:
dig a +short hostname.ddns.netYou will need to replace ‘hostname.ddns.net’ with your actual hostname that you chose.
We must now configure CSF/LFD on our server to recognize and whitelist our hostname.
Configure CSF/LFD for DynDNS (Steps 4-6)
We must first edit the file csf.dyndns and add the hostname of your no-ip account. You can use nano or vim via SSH, or request that the Knownhost Support team does this for you.
nano /etc/csf/csf.dyndns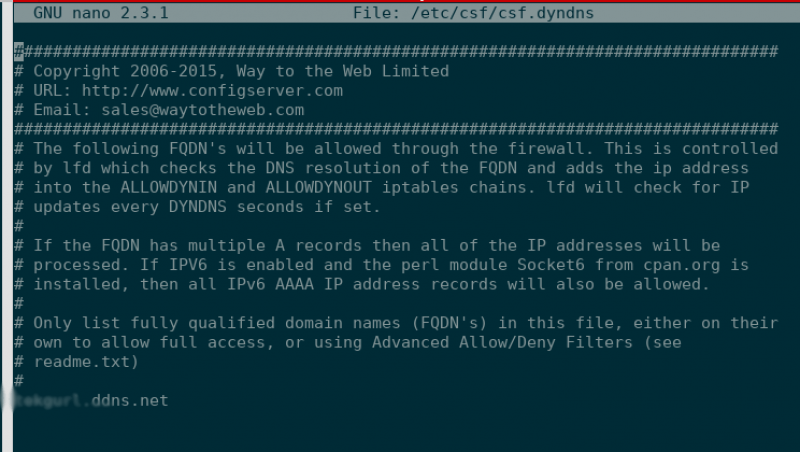
Once you have made the desired changes to the file, use Ctrl X to exit. You may be prompted to confirm your changes and the file name.
Next, we will need to edit the CSF/LFD configuration file.
nano /etc/csf/csf.confYou can use Ctrl W to search for the settings that need to be changed since this file is quite large compared to the last. Pictured below is the section of the file that we will be editing.
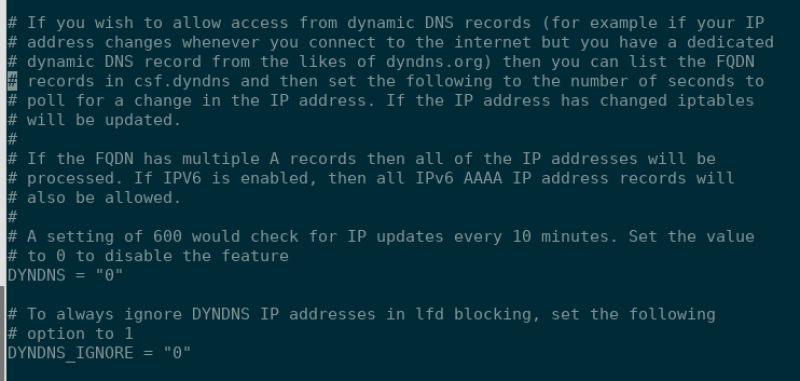
We will change “DYNDNS_IGNORE = 0” to “DYNDNS_IGNORE = 1” and then change “DYNDNS = 0” to whatever value to choose. I will change mine to 300:
Now, we just need to restart the firewall:
csf -ra
This concludes the firewall configuration portion required to set up DynDNS.
Let’s test to make sure I am now being ignored by the firewall. First, check to make sure your IP isn’t already whitelisted in the firewall using the following command (replacing XXX.XX.XX.XXX with your actual IP:
csf -g XXX.XX.XX.XXXIf it is whitelisted, remove the rule with the following:
csf -tr XXX.XX.XX.XXXNow you may test to make sure you are whitelisted due to DynDNS and not due to any previous rules added. To test, I repeatedly attempted to log in via SSH as root using the wrong password while tailing the LFD logs. You may tail, or watch, the LFD logs via SSH with the following command:
tail -f /var/log/lfd.logI’m watching the LFD firewall logs while I do this to see if my failed attempts are being ignored because we configured the firewall to ignore the hostname (or the IP associated with the hostname, technically). Here is what I saw when tailing my firewall log, which proves that we were successful in configuring DynDNS:
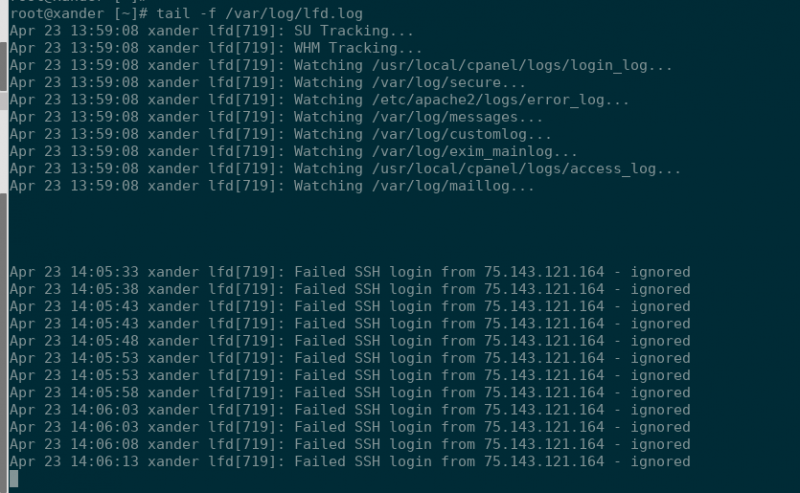
Notice that it states that my failed attempts are being ignored. Thus, DynDNS was registered, installed, and configured successfully on my computer, and CSF/LFD was configured correctly to ignore any attempts via my DynDNS hostname.