Email Best Practices: Email Design & Feedback Loops
Last Updated: January 20, 2022
- Email Best Practices: Avoiding the Spam Box and Blacklists
- Email Best Practices: Mail Server Configuration
- Email Best Practices: Email Design and Feedback Loops
The design of an email is important to consider. A compelling email subject, or ‘call to action’, can determine whether or not the email is even opened by the recipient. A good design that mimics the design of your site will make the email more recognizable. Designing the actual email could involve configuring the correct image to text ratio, personalizing your content (as with mimicking the site’s design within the email itself), sending a copy of the email in plain text and in HTML, ensuring that any included HTML complies with HTML standards, structuring email so that the contents of your email relate to the subject of the email, testing email rendering on various clients and browsers, ensuring you include the unsubscribe link, using an actual email address to reply to instead of a “no-reply” email address, limiting the number of different fonts and font sizes to 3 or fewer, and personalizing the greeting with the client’s name. Designing an email can be quite involved and require coding/web development skills. I advise ensuring that any site development/design services you purchase include the corresponding site’s email design as well if you plan to use your domain to send emails.
Another consider when designing email is how legitimate functionality may be abused. For example, if your contact or registration forms include the original message, a spammer may abuse your forms by entering the spam subject in the subject field, and then entering target email addresses of their choosing (of which they do not own) so that the spam content is sent to them as part of the contact form message. The Mail Delivery Failed message may look like this:
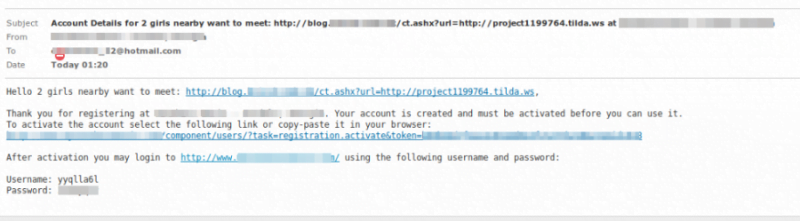
Notice in the example above that the vector used for the spam payload delivery is a legitimate function of the registration form, of which includes the original message in the registration email. The original message is shown prior to the registration details sent in the reply. This is an example of both how important it is to be careful when formatting the design of the message and of a legitimate script being used maliciously.
One possible solution would be to remove the copy of the original message from the communication. Another possible solution would be to scan *ALL* outgoing messages from the server for spam, though this could result in some false positives and would use more resources on the server. Another possibility would be to force email validation on those submitting the forms by sending a verification code to the email they specify and then having them enter it to validate the form submission. They could technically send a lot of verification codes out from the server, however, they are likely to stop since they won’t be able to use the forms. Removing the original message from the communication is likely the best option simply because the email verification method can lead to email accounts being spammed with unwarranted verification codes and scanning all outgoing messages may miss some of the messages of the scanner is configured too lax. Removing the original message removes the vector of attack.
Feedback loops and PostMaster Tools
The following tables gives information on some major mailservers’s PostMaster Tools and Feedback Loops that you will want to sign up to. Signing up with these will help you manage your IP reputation and notify you of any problems with the email you are sending.
| Provider | Email Best Practices | PostMaster Tools | Feedback Loop |
| AOL | postmaster.yahooinc.com/best-practices | postmaster.yahooinc.com/ | postmaster.yahooinc.com/cfl-request |
| AT&T | www.att.com/esupport/postmaster/best-practices/index.jsp | www.att.com/esupport/postmaster/index.jsp | |
| Gmail | support.google.com/mail/answer/81126?hl=en&ref_topic=7279058 | support.google.com/mail/answer/6227174?hl=en&ref_topic=6259779 | support.google.com/mail/answer/6254652?hl=en&ref_topic=7279058 |
| Microsoft | sendersupport.olc.protection.outlook.com/pm/policies.aspx | SNDS and Junk Email Reporting Program now combined | sendersupport.olc.protection.outlook.com/snds/index.aspx |
| Verizon | same as AOL | same as AOL | same as AOL |
| Yahoo | help.yahoo.com/kb/bulk-email-industry-standards-practices-sln3435.html | help.yahoo.com/kb/postmaster | postmaster.yahooinc.com/cfl-request |
For several other mail server providers, you have the option to sign up for a single Feedback Loop that provides information for them all, or you can sign up to each individually. Given the several listed in the table above that you will have to manage independently, it makes sense that you would want to manage as many as possible via a single Feedback Loop. Luckily, Return Path offers a Universal Feedback Loop, which can be used to manage all of the following FBLs in one location:
- Bluetie/Excite
- Comcast
- Cox
- Fastmail
- LaPoste.net
- Libero (Italiaonline)
- Locaweb
- Mail.ru
- OpenSRS/Hostedmail (Tucows)
- Rackspace
- Synacor
- Telenor
- Telstra (use the Universal Feedback Loop to apply)
- Terra
- UOL
- BAE Systems (USA.net)
- XS4ALL
- Yandex
Conclusion
Properly configuring and maintaining a mail server does require some effort, but don’t be discouraged. Remember that your KnownHost support team is here to help you!