What Are the Most Common Reasons Hackers Will DDoS Sites?

Brian Krebs. OVH. Dyn. And the open-sourcing of the code of the botnet that attacked them. Are you DDoS-defending your business? If not, now is the time.
- A supercharged botnet
- 7 reasons DDoS is popular among hackers
- Action to DDoS-defend your business
A supercharged botnet
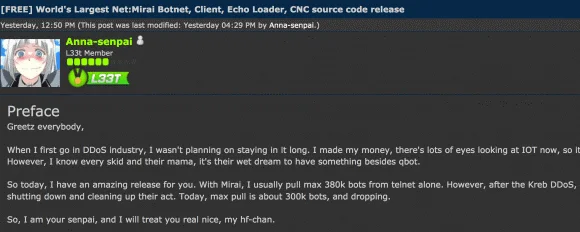
The Mirai botnet has been busy lately. In September, it was used for a couple of massive attacks, one against US-based security journalist Brian Krebs, the other against French web host OVH. In October, the network of IoT devices that make up its bot army (some 380,000, according to its purported author) were used to DDoS Dyn and temporarily cripple a large chunk of the internet in the United States.
But, unfortunately, it gets worse… much worse. Security thought-leaders are sounding the alarm bell after a hacker publicly released the source code for Mirai. After all, the scope of the DDoS attacks from Mirai are highly disturbing. The one that hit Krebs measured 620 gigabits per second. The one that hit OVH measured 1.1 terabits per second. If you are having trouble grasping that sheer attack volume, it’s understandable: Mirai delivers almost unimaginable information-overload by our current standards.
Mirai is getting the press, but Bashlight is the original, explained Dan Goodin of Ars Technica. “Until now, the botnets created with the newer and technically more sophisticated Mirai have been greatly outnumbered by those based on its rival Bashlight,” he said, “with about 233,000 infected devices versus 963,000 respectively.”
The release of Mirai’s code – via the user Anna-senpai on Hack Forums (a site that has since been accused of running a DDoS-for-hire service) – is troubling to security pros because easy access means proliferation of gigantic DDoS assaults.
Goodin noted that there has been an increased focus among those who use botnets to target CCTV cameras, routers, thermostats, webcams, and other vulnerable IoT devices. Once formed, the army of slaves is used to extract ransom from victims (in exchange for halting a DDoS).
“Both Mirai and Bashlight exploit the same IoT vulnerabilities,” said Goodin, “mostly… weakness involving the telnet remote connection protocol in devices running a form of embedded Linux known as BusyBox.”
One reason Mirai has become more prominent, though, is that it encrypts communications it sends to central command (i.e., the master). Also, some believe that the conversion of some 80,000 of the 963K Bashlight devices to Mirai suggests that the newer malware may be overtaking and then patching devices so that other botnets can’t reclaim them.
Although the open sourcing of the code is especially troubling, the attack on Dyn should also not be overlooked when we consider the power that is currently in the hands of botnet operators. Mirai successfully sabotaged the DNS provider Dyn and brought its response time to a crawl (or at least a large portion of the attack came from Mirai slaves). According to Michael Kan of Computerworld, many in the security community think that the Dyn DDoS (2 attacks of 130 minutes and 70 minutes, divided by a 2 ½ hour break) was more of a warning shot than an actual siege: it just leveraged 100,000 devices of the half-million or so devices then available.
7 reasons DDoS is popular among hackers
Why are these attacks becoming such a common form of malicious intrusion?
Reason #1 – Easy as 1, 2, 100 thousand
One reason DDoS is a go-to for hackers is that it’s simple, and it works. The Dyn attack sidelined household-name web giants such as Spotify, Netflix, Airbnb, and Twitter, all of which use Dyn to connect their site to users.
“It doesn’t take particularly advanced hacking skills to block access to those sites,” said Emma Hinchliffe. “It just takes a huge network.”
Well, how do you access a huge network? Even before the open sourcing of Mirai, the simplicity of carrying out a DDoS has been troubling to those who protect networks. Through paid services, anyone is able to rent a botnet. In fact, the criminally oriented can even have a stressor or booter service do the dirty work for them.
It is often challenging for the security team or law enforcement to track down the booters because they use proxies to assault you from different locations.
Reason # 2 – Cash for peace
DDoS-for-ransom, a form of extortion, has been on the rise over the last few years. Essentially you get barraged by traffic, see your site go down, and then get a note letting you know that you can regain your smoothly functional site for a certain amount of Bitcoin.
Security experts recommend never paying the attackers because there is no guarantee they won’t do it again and because it feeds the growth of the problem; however, some site owners feel they have no choice to get their own revenue coming in again.
Reason #3 – Slash-and-burn competition
What’s one way to outperform the rivals in your industry? Well, you could make it impossible for them to operate.
“Just small amounts of downtime can end up costing a company thousands [or millions] of dollars,” noted Christian Sager. “It can also promote negative associations with a brand, so that customers no longer trust their services.”
Reason #4 – Hacktivism
DDoS isn’t always just about pummeling someone for money. It’s also a way that some actors use to voice dissent. South Korea, the U.S., Russia, and Georgia have historically been DDoS targets. Keep in mind that many of these attacks are thought to be perpetrated by other nations – which makes them more cyberwarfare than citizen protest. However, individuals do sometimes DDoS governments or companies because they disagree with them ethically.
Reason #5 – Rise of the “script kiddy”
Some of those behind DDoS events have been given the derisive name “script kiddies,” highlighting the fact that they lack technical skills (instead grabbing a script in a forum) and have what are viewed as immature intentions.
For instance, game publishers are sometimes DDoSed immediately following an update, because an irritated player believes they “nerfed” the best part.
“Also, let’s be honest, being able to take out a company from your bedroom is probably amusingly empowering in a David and Goliath sort of way,” said Sager. “Today’s DDoS is yesterday’s vandalism.” (Note that he made these comments in 2014, when DDoS was much less destructive and economically devastating than it is today.)
Reason #6 – The overpowering decoy
A DDoS is certainly more uncontrollable than a fake duck that you can throw in your hunting bag, but it is sometimes a decoy in the sense of a distraction. In these cases, the directness and crudeness of a DDoS is used as a cover for a more technical, surgical hack. A landmark incident of this Ocean’s-11-style assault occurred in 2013, when a botnet operator slammed the Bank of the West with fraudulent requests while they entered an account and withdrew $900K.
Reason #7 – This is only a test…
A company will occasionally force itself offline – whether by accident or when intentionally resilience-testing their systems.
Game servers are not exempt from DDoS. It’s an easy way to gain advantage over competing players in player vs player competition. Learn more about the dedicated game servers from KnownHost.
Action to DDoS-defend your business
In the post-open-sourcing of Mirai, heavyweight DDoS has become more widely available than ever before. And people continue to have various reasons to want to crash websites.
In this increasingly volatile climate, are you DDoS-defended? At KnownHost, we offer complimentary DDOS protection on all VPS and SSD VPS product lines. See how you’re protected.